Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
thoughts on @GMX_IO 's exploit. Spending 20 minutes on this might save you from an exploit.
- A reentrancy attack is common in solidity-based smart contract and root cause of @GMX_IO 's hack. it's not new neither easy to avoid in evm based smart contract
- Sui move the language itself was designed in an object-centric model - this prevents sui move-based smart contract from suffering such risks
heartfelt to see what happened to @GMX_IO as it has inspired lots of new ideas' initiations.
Operating Defi is risky and I would seriously recommend that new defi builders to run in more robust language, or at least spend hours researching what a reentrancy attack.
I also wrote this and hopefully this helps:
What is Reentrancy Attack and why it does not happen in Sui Move:

10.7. klo 00.40
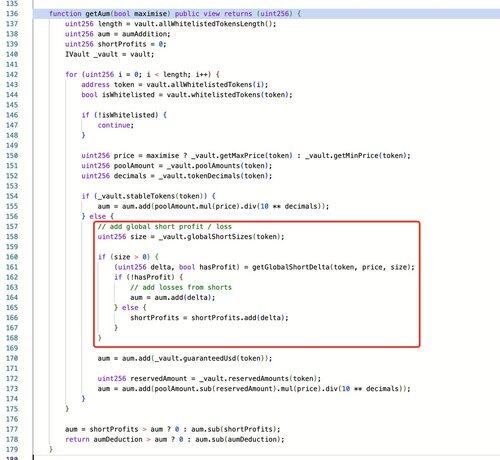
The root cause of this attack stems from @GMX_IO v1's design flaw where short position operations immediately update the global short average prices (globalShortAveragePrices), which directly impacts the calculation of Assets Under Management (AUM), thereby allowing manipulation of GLP token pricing.
The attacker exploited this design vulnerability by leveraging the Keeper's ability to enable `timelock.enableLeverage` during order execution (a prerequisite for creating large short positions). Through a reentrancy attack, they successfully established massive short positions to manipulate the global average prices, artificially inflating GLP prices within a single transaction and profiting through redemption operations.
5,28K
Johtavat
Rankkaus
Suosikit

