What is ZK technology? How zero-knowledge boosts blockchain security and scalability
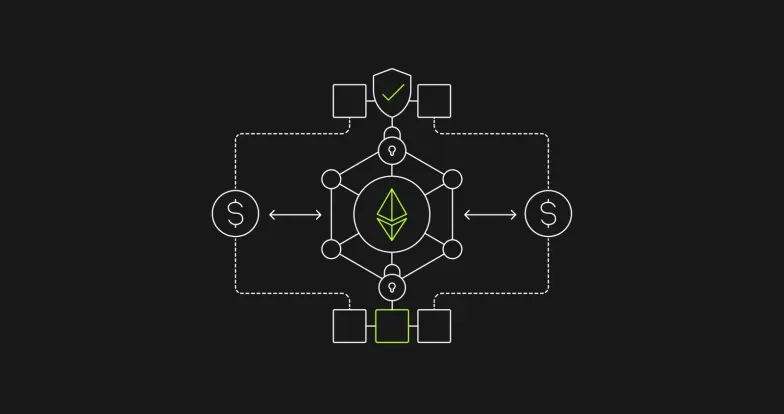
Zero-knowledge (ZK) technology refers to a cryptographic method that allows one party to confirm the proof of a statement without revealing any information beyond the statement of truth itself. In short, it helps to increase confidentiality and safeguard digital transactions.
ZK proofs in particular are essential for enhancing security across various applications of cryptography, such as voting, blockchain transactions, and identity verification — limiting the possibility of data breaches and deceitful activities. You may have heard about ZK proofs in the context of ZK rollups. ZK rollups allow Ethereum transactions to be bundled together and executed on Layer 2, reducing congestion on the mainnet. ZK proofs, meanwhile, confirm these transactions have been made, so the blockchain can be updated.
Over the last two years, ZK technology has increasingly been perceived as an essential piece to solve the blockchain trilemma by supporting scalability and interoperability without compromising on privacy. Read on to learn how ZK works and discover some of the top projects applying it today.
TL;DR
ZK rollups enhance blockchain scalability by batching transactions and using ZK proofs to keep transaction details confidential.
ZK protocols protect transaction confidentiality by allowing a prover to verify a statement's validity to a verifier without disclosing any extra details.
ZK proofs support blockchain interoperability by allowing confidential cross-chain transactions and communication to take place without revealing transaction specifics.
Top ZK Layer 2 projects in 2024 include X1, StarkNet, zkSync, and Loopring, showcasing applications for scalability, privacy, and Ethereum compatibility.
ZK technology in decentralized finance (DeFi) increases security, privacy, and efficiency through features like private transactions, confidential smart contracts, and scalable decentralized applications (DApps).
What are ZK rollups and how do they enhance scalability?
Helping address the issue of blockchain scalability, ZK rollups offer a unique method for managing the increasing demands on blockchain networks. As a Layer 2 scaling solution, ZK rollups combine multiple transactions into a single "batch," which is then executed on the primary blockchain. The key to this process is the implementation of ZK proofs, a type of cryptographic verification that enables the batch of transactions to be authenticated without compromising the privacy of each transaction. The main benefit of ZK rollups is their ability to significantly improve scalability. This is achieved by treating multiple transactions as a unit, considerably reducing the space they take up on the blockchain.
This reduction leads to several beneficial outcomes: an increase in throughput, meaning more transactions can be processed in a shorter timeframe; a decrease in transaction costs, making blockchain technology more accessible and affordable; and an overall boost in blockchain efficiency, providing faster and more reliable transactions.
By implementing ZK rollups, the scalability limitations that have hindered blockchain progress are being addressed while maintaining the decentralized and secure features essential for their widespread adoption and long-term success. Striking a balance between efficiency and protection is vital for advancing blockchains.
ZK rollups represent a pivotal advancement in blockchain scalability. Through the innovative use of batched transactions and zero-knowledge proofs, they offer a solution that not only enhances throughput and lowers costs but also preserves the foundational principles of blockchain technology: decentralization, security, and transparency.
How do ZK protocols guarantee privacy in transactions?
ZK protocols use cryptography to increase transaction privacy, particularly on the blockchain. They allow the "prover" to demonstrate the accuracy of a statement to the "verifier" without disclosing any information other than the statement's truth. This cryptographic method conceals data, protecting the privacy of transaction details. ZK protocols are founded on three principles:
Completeness
Soundness
Zero-knowledge
Completeness allows a prover to effectively prove the truth of a statement to a verifier. Soundness makes sure that any attempt by a dishonest prover to convince a verifier of a false statement will be unsuccessful. Finally, zero-knowledge guarantees that the verifier gains no additional information other than the truth of the statement, therefore maintaining the confidentiality of the transaction's details.
The versatility and importance of ZK protocols in providing secure transactions is seen in various aspects of the blockchain and cryptocurrency industry. For example, Zcash uses zk-SNARKs (zero-knowledge succinct non-interactive argument of knowledge), a type of ZK proof, to enable confidential transactions without revealing information about the sender, receiver, or transaction amount.
ZK proofs have a crucial function in guaranteeing the authenticity of data while maintaining its secrecy. This is especially advantageous for cloud storage platforms, as it confirms the accuracy of data storage on external servers without revealing the actual data. Meanwhile, in password authentication, ZK proofs offer a reliable and effective way of verifying user identities without revealing passwords, reducing the potential for security breaches.
The development of ZK protocols has brought about different versions, each with its own benefits and drawbacks regarding proof size, prover efficiency, and verification speed. Some noteworthy variations include zk-SNARKs, zk-STARKs (zero-knowledge scalable transparent argument of knowledge), PLONK, and Bulletproofs. These examples are tailored to meet specific requirements, whether it's for enhancing privacy in transactions, scaling blockchain networks, or supporting the development of secure and efficient Layer 2 solutions.
What role do ZK proofs play in interoperability among blockchains?
Developed in the 1980s, ZK proofs help to make blockchain networks compatible, allowing for the seamless transmission of information and assets while also protecting confidentiality and security. Alongside its ability to protect the security of data as explained above, this essential cryptographic instrument plays a crucial role in enabling cross-chain compatibility.
ZK proofs serve as a bridge between diverse blockchain systems, enabling them to operate seamlessly within a larger, interconnected environment. This expands the potential for DeFi services and applications that can function easily across different blockchain platforms, while maintaining transparency and security.
Two forms of ZK proofs exist — interactive and non-interactive — and each is designed for different situations. Interactive proofs involve communication between the prover and the verifier to confirm the validity of a statement. Non-interactive proofs, meanwhile, allow the prover to gain authentic proof without interacting with a verifier. This adaptability makes ZK proofs a versatile solution for addressing diverse privacy and security concerns in blockchain technologies.
Although ZK proofs have great potential, they also face certain challenges. One difficulty is their high computational demands, especially for intricate proofs, which may negatively impact scalability. Another obstacle to widespread use is the complexity of ZK proofs, as the tool requires specialized expertise to be implemented. However, ongoing research and technological progress are tackling these issues, making ZK proofs more practical and effective for achieving blockchain interoperability.
Top zero-knowledge Layer 2 projects in 2024
As the popularity of Zk solutions has grown, several top crypto projects leveraging them have emerged. These are some of the top projects using ZK elements in 2024:
X Layer: OKX's own ZK Layer 2 network, X Layer, uses ZK proofs to make it cheaper and faster for millions of users to interact with on-chain applications. Built with the Polygon CDK, X Layer provides improved security and scalability. It also supports Ethereum compatibility for effortless deployment of DApps using the EVM.
StarkNet/StarkEx: STARKs are employed to enable scalable and confidential transactions, with a particular focus on decentralized exchanges and overall computation.
zkSync: A ZK rollups-based approach for scaling at Layer 2, enabling rapid and affordable transactions on Ethereum.
Loopring: Specializes in decentralized exchanges, which use ZK proofs to support scalability and security in cryptocurrency trading.
Aztec/Aztec Network: By applying ZK rollups, privacy and scalability are combined for Ethereum transactions, providing greater confidentiality.
Immutable X: ZK rollups are used to achieve faster confirmation times and low transaction fees for NFT trading and minting.
Scroll: A ZK rollup approach that prioritizes fast processing and minimal delays, designed to work seamlessly with the EVM.
Mina protocol: Boasts the lightest blockchain in the world, using ZK-SNARKs for effective and expandable transactions.
Syscoin: Provides a blockchain-based platform that prioritizes scalable smart contracts and safe issuance of tokens, using ZK proofs to enhance transaction speed.
What are the applications of zero-knowledge in DeFi?
Many believe that ZK technology can be a powerful force in the continued emergence of DeFi. Central to the DeFi ethos is a desire to create a more open and equitable financial system. However, concerns have been raised about the privacy of transactions. ZK technology can help address these concerns while simultaneously supporting growth for DeFi.
Private transactions: ZK technology enables safe and private transactions while protecting sensitive data from exposure.
Confidential smart contracts: The technology also supports the functionality of smart contracts in a confidential way.
Scalable DApps: ZK proofs support DApps in managing a higher volume of transactions effectively, encouraging wider acceptance.
Through the use of ZK technology, DeFi platforms are better equipped to provide enhanced security, privacy, and efficiency. In doing so, developers can expand the capabilities of their projects and potentially reach more users, boosting adoption of DeFi at large.
The final word
Today's ZK Layer 2 protocols are an advancement in blockchain technology that tackles the urgent issues of scalability, privacy, and interoperability. By allowing for faster and more secure transaction and computation processing, these protocols greatly increase the efficiency of blockchain networks. And as the adoption of blockchain networks continues to grow, the influence of ZK technology can't be understated.
Faster, more secure, and scalable transactions could be the key to unlocking wider adoption for blockchain technology, as the benefits become too great for users and entities to overlook. Meanwhile, as developments continue, fresh innovation and new functionality could be right around the corner — as evidenced by the top zero-knowledge projects listed in this article.